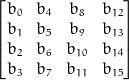
AES
AES (Advanced Encryption Standard) is the standard way to encrypt large amount of data. AES is in the family of ciphers called Rijndael ciphers, and is a symmetric key algorithm meaning it uses the same key to encrypt and decrypt data. It encrypts data in blocks of 128 bits, with key sizes of 128, 192, or 256 bits.
How it encrypts data:
The algorithm uses the following steps:
Depending on the key size, diffrent number of rounds is used to ensure every bit of the output is depending on every bit of the key:
The 128 bits of data, is represented as a matrix of the form below:
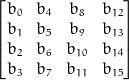
So the first 4 bytes represents the first column.
Key expansion:
In the key expansion step we generate a number of round keys, from one short key. Since we use a round key in the initial round, the standard rounds and the final round, we need one more round key than we have cycles. We generate these keys with the Rijndael key schedule algorithm.
Add key step:
The add key step, xors the current state of the matrix with the round key (for this round) found in the key expansion step. This is done byte for byte, as illustrated below (here  is the input,
is the input, 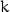 the key and
the key and 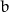 the output).
the output).

Substitute bytes:
In the substitute bytes step, each byte is substituted with another byte according to a lookup table 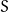 . No bytes in this lookup table maps to itself
. No bytes in this lookup table maps to itself 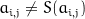 , further more no bytes maps to their inverse
, further more no bytes maps to their inverse 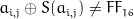 . The process is illustrated below, together with the lookup table:
. The process is illustrated below, together with the lookup table:

Shift rows:
The shift row step, shifts the rows a diffrent amount. The first row does not shift at all, the second row shifts 1 byte to the left, the third row shifts 2 bytes and the fourth row shifts 3 bytes. This step is important because it mixes the columns, without this step AES would just encrypt four independent blocks. The step is illustrated below:

Mix columns:
In the mix columns step we transform each column, in a way so that every output byte depends on every input byte. This is done kind of like a matrix multiplication, except instead of the plus operation we use the xor operation, and instead of normal multiplication we use multiplication in a Rijndael's finite field. This step, and the diffrent operations is illustrated below:
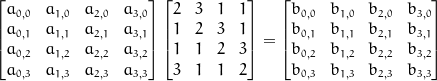
Normally we would multiply a column and a matrix like this:
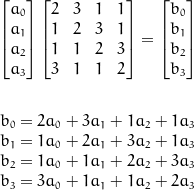
But remember we use xor and multiplication in a Rijndael's finite field, so we get:

Security:
“The design and strength of all key lengths of the AES algorithm (i.e., 128, 192 and 256) are sufficient to protect classified information up to the SECRET level. TOP SECRET information will require use of either the 192 or 256 key lengths. The implementation of AES in products intended to protect national security systems and/or information must be reviewed and certified by NSA prior to their acquisition and use.”
CNSS Policy No. 15, Fact Sheet No. 1
So its safe to say its secure, or at least USA think so 😈😈…
Related topics:
Rijndael cipher
Symmetric key algorithm
Rijndael key schedule
Rijndael's finite field